HOW TO BUILD SIEM AZURE SENTINEL
Cybersecurity Home Lab
By Tavaras Pinckney on September 03, 2023
In this blog, I will be giving step-by-step instructions on how to build an SIEM using Azure Sentinel.
The purpose of this content is to gain hands-on experience and practical knowledge of what the day and life of an SOC Analyst is like. The key objective of this lab is to extract data using API from Windows Event and Security Viewer. Then ingest that data into Azure Log Analytics, and finally map out the raw data in Azure Sentinel. I will be providing as many screenshots as possible for each step taken and descriptions to give a clear understanding of this process.
A SIEM helps organizations detect, analyze, and respond to security threats before they harm business operations. Our objective is to build an SIEM system in a virtual environment utilizing a personalized PowerShell script that extracts metadata from the Windows Event Viewer and forwards it to a third-party API for geolocation information. We will set up the Log Analytics Workspace in Azure to receive custom logs that contain geographical data such as latitude, longitude, state/province, and country. Finally, we will configure the Azure Sentinel Workbook with a custom script to exhibit global RDP brute force attack data on a world map, sorted by location and attack. After building the SIEM we will have a live visual of real-time attacks from failed RDP attempts from our Virtual Machine.
STEP 1: CREATE AZURE SUBSCRIPTION
Set up a Microsoft Azure FREE trial account. You will get a $200 credit for the first month, which will be well enough to do this lab.
STEP 2: CREATE VIRTUAL MACHINE (VM)
On the Home screen CLICK on Virtual Machine and then Create.
Under Resource Group CLICK Create New. Name group Honeypotlab or (whatever you feel is suitable.)
Change Region to (US West US 2).
Change Image to (Windows 10 Pro, version 22H2-x64 Gen2)
CLICK Password under Administrative account. Then change your Username and Password. (Make sure you remember the PASSWORD for you will need it later to log into the virtual machine.)
Select inbound ports (RDP 3389).
CHECK I confirm.
Click NEXT twice until you're under the Networking Tab.
Under NIC network security group CLICK Advanced. Under Configure network security group CLICK Create new.
Remove Inbound Rules. CLICK Add an inbound rule.
Under Destination port ranges put a (*) in the space this will indicate any ports!
Under Destination port ranges put a (*) in the space this will indicate any ports!
Change Priority to (100)
Change Name to (Danger) or anything that is suitable for you. Then CLICK Add.
The purpose of this is to ALLOW all traffic into the VM.
CLICK Ok
Then CICK Review + Create.
Then CLICK Create
STEP 3: CREATE LOG ANALYTICS WORKSPACE
The purpose of this section is to create our own custom log to generate a geolocation of where the attacks are coming from.
GO to the search bar and type in Log Analytics Workspace.
Click Create New. Under Resource group Click HoneypotLab (or whatever name you named your resource group.)
Under Name insert (law-honeypot1) or whatever name you choose. Then CLICK Review and Create. Then Create.
STEP 4: ENVIRONMENT SETTINGS
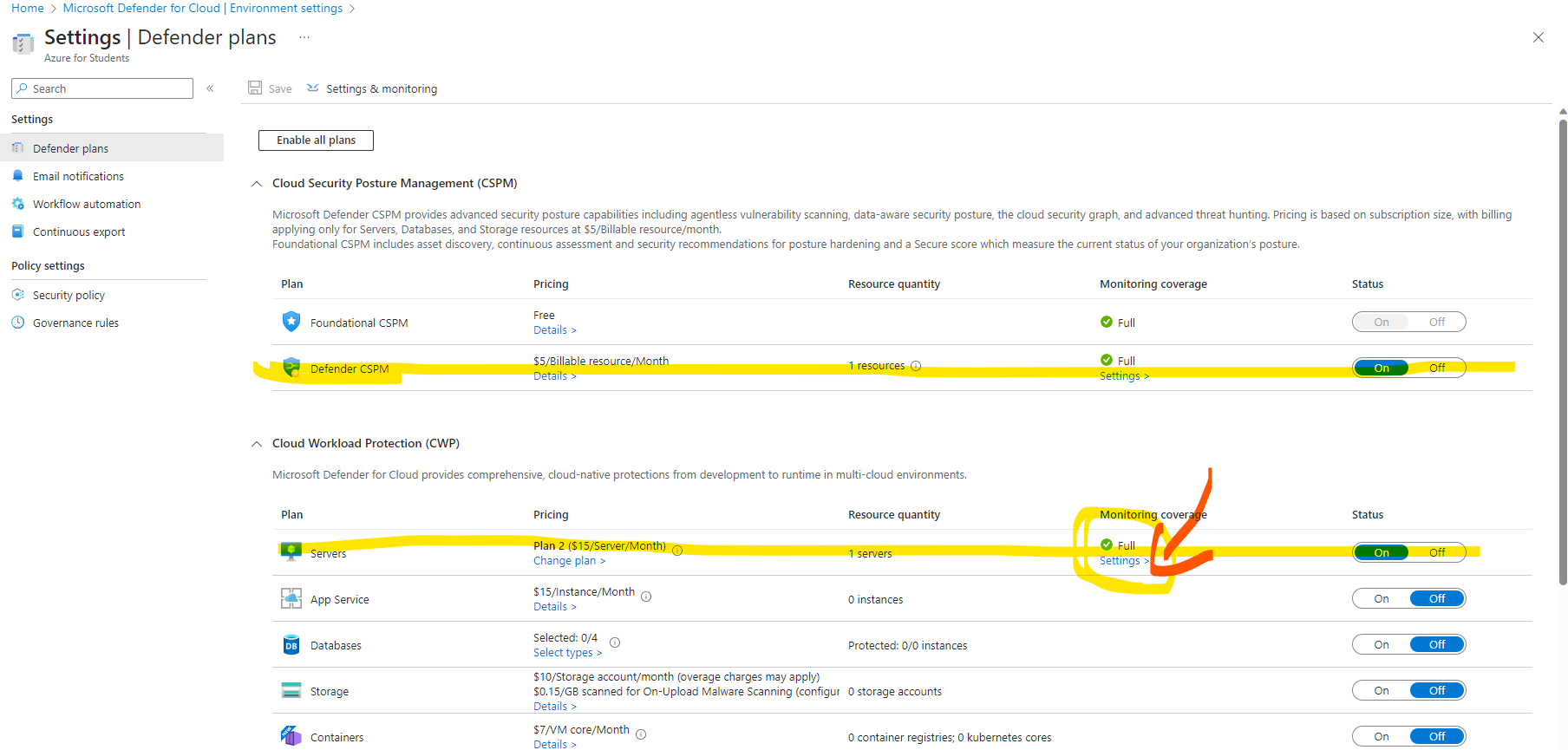
GO to the search bar and type in Microsoft Defender for Cloud.
Then under Management Click on Environment settings.
Under name CLICK the drop-down arrows until you see your Azure account. Then CLICK on the account name.
Under Plan go to Defender CSPM and CLICK On (to turn on).
Under Plan Turn S(Servers) On. Then CLICK Settings.
STEP 5: Connect VM
Go back to Log Analytics Workspace. CLICK on the workspace you created.
On the left-hand side scroll down and CLICK Virtual Machine. Click on the machine and make sure it's connected. If not CLICK on connect.
The purpose of this is to create a visual view using a SIEM.
GO to the search bar and type in Microsoft Sentinel.
CLICK on Create then choose the Log that you created. Then CLICK Add.
STEP 7: Log into VM
Go back to Virtual Machine in the search bar.
CLICK on VM.
Then CLICK Connect.
Under Credentials CLICK (More choices.)
Then CLICK (Use a different account) and enter the username and password we created before.
For demonstration purposes attempt one failed Login by entering the wrong password. Then Enter the correct password to successfully logon.
STEP 8: Event Viewer
This step is just to give you an idea of what we will be looking for in the next steps.
Then go to the search bar and type in Event Viewer. CLICK on (Windows Logs) and CLICK (Security.)
Expand the (Keywords) section to see all of the Audit information.
When you scroll down a little you will see the failed attempt that we've done when Login to RDP (Look for Event ID 4625).
Below you can see the information we gathered from the Event Viewer. We capture the Failure Reasons, Workstation Name, and IP Address of possible attackers.STEP 9: PING VM & FIREWALL SETTINGS
The purpose of this step is to allow outside traffic to discover the VM quickly.
GO back to YOUR desktop open Command Prompt (CMD) and try pining your VM. You'll see that the Request timed out.
Go to the search bar on VM and type in (Windows Defender Firewall with Advance).
When opened CLICK on (Windows Defender Firewall Properties).
Turn Off the Firewall state in the Domain Profile, Private Profile, and Public Profile.
STEP 10: Add PowerShell Script and Get API
Try Pinging the machine again to make sure its packets go through.
The purpose of this step is to set up the PowerShell script with API to be able to pull the Geolocations of the attacker. This script will generate the live longitude, latitude, and IP Address of an attacker from the Event Viewer Security Log when there is a Failed Log On. The Log file will then be output into the C:\ProgramData\, which is a hidden folder in the VM File Folder. You will need to replace your API in the Script with your own Key. The steps are below.
Open PowerShell ISE on VM.
CLICK (File) then (New)
Copy and Paste the Script from the link.
Save on Desktop as (Log Exporter).
 |
Keep in mind the Free Version only allows 1,000 requests per day. Which isn't a lot when attackers start discovering your machine. the paid version is $15 and allows 150,000 requests.
Copy your API and Paste it in the second line of the PowerShell Script $API_KEY = "0000000000".
CLICK the GREEN Play button to RUN the Script. An error may pop up but just give the script some time to run. The PURPLE data is from Failed Attempts to log on.
The Script then grabs the Data and sends it to the API IP Address then generates a Failed Log File in the File Folder in the VM. The first few lines will be sample data that we receive we're going to use this data to train Analytics Workspace on how to grab the data.
The folder you will look for is hidden. To unhide the folder simply go to File Explore.
CLICK on (View). Then check the Hidden Files box to the right.
To get to the File CLICK on (This PC).
Then CLICK on (Windows C:)
Then CLICK on (Program Data) and at the bottom of the files you should see the (Failed RDP) file.
Double-click and open it.
STEP 11: CREATE CUSTOM LOG IN LOG ANALYTICS
The purpose of this step is to set up a log that brings in the custom geo log into the Log Analytics Workspace. We will be extracting RAW data from our VM and loading it onto Azure. This step is the mapping phase where we have to extract the raw data to plot the geo location on a map..
Go back to MS Azure.
Go to Log Analytics Workspace.
CLICK on (law-honeypot) or whatever you named your resource.
On the left-hand side CLICK on (Tables).
CLICK on (Create). Then Choose (New custom log (MMA-based)
Verify that the info looks correct. Then CLICK (Next).
Change Type to (Windows) then paste the folder from the VM where the log is located under Path (C:\ProgramData\failed_rdp.log). $$$MAKE SURE TO TYPE THAT IN CORRECTLY OR LOGS WILL NOT BE PULLED IN)
Then CLICK (Next).
On the left-hand side CLICK on (Logs).
On-Line 1 Type in FA
FAILED_RDP_WITH_GEO_CL should populate.
Wait for about 10 minutes before CLICKING (Run).
STEP 12: EXTRACT RAW DATA TO PLOT GEO LOCATION ON A MAP
Final Step
As you can see the custom log has now loaded a lot of the data from the Failed RDP Log.
Now it's time to Extract the data. For this step, we will be extracting the Lattitude, Longitude, Country, and State/Province with a PowerShell Script to plot Geo Locations on a map.
Now that the Failed RDP Log has loaded.
Scroll down on the left-hand side and CLICK on (Workbooks).
CLICK (Create)
Paste this Script and then CLICK (Run).
FAILED_RDP_WITH_GEO_CL
| extend username = extract(@"username:([^,]+)", 1, RawData),
timestamp = extract(@"timestamp:([^,]+)", 1, RawData),
latitude = extract(@"latitude:([^,]+)", 1, RawData),
longitude = extract(@"longitude:([^,]+)", 1, RawData),
sourcehost = extract(@"sourcehost:([^,]+)", 1, RawData),
state = extract(@"state:([^,]+)", 1, RawData),
label = extract(@"label:([^,]+)", 1, RawData),
destination = extract(@"destinationhost:([^,]+)", 1, RawData),
country = extract(@"country:([^,]+)", 1, RawData)
| where destination != "samplehost"
| where sourcehost != ""
| summarize event_count=count() by latitude, longitude, sourcehost, label, destination, country
To change the view of the data CLICK on (Visualization) Change to Map.















































Comments
Post a Comment